NACTF 2020 Walkthrough — CTF’s Solutions

What is “NACTF” ?
Newark Academy CTF (NACTF) is an online jeopardy-style cybersecurity competition hosted by Newark Academy’s Computer Science Club. Form teams with up to 5 members and win awesome prizes! Teams compete to decrypt, hack, or reverse engineer challenges in topics like cryptography, forensics, and binary exploitation. Participation is open to anyone but prizes are restricted to US middle school and high school students.
Task : Reverse Engineering (Generic Flag Checker® 175)
Description :
Flag Checker Industries™ has released their new product, the Generic Flag Checker®! Aimed at being small, this hand-assembled executable checks your flag in only 8.5kB! Grab yours today!
link:
https://www.nactf.com/files/8b8f176882de90468669fb223fcc607f/gfc1
Solution:
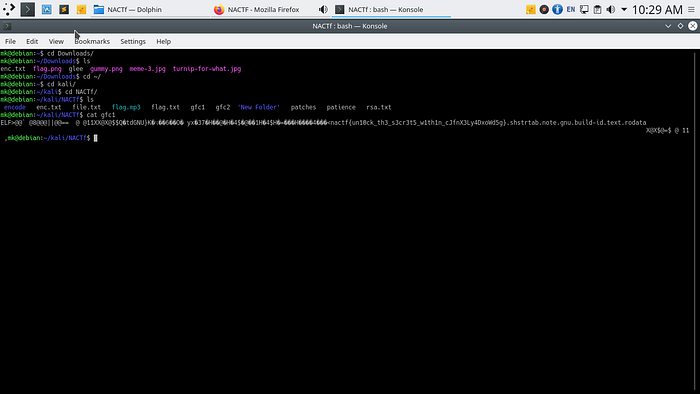
The task is to reverse engineer the given file to find the hidden flag in it. The first basic thing to analyze is the source code of the given file, you can just simply “cat” the given file’s (gfc.executable) source code which just reveals the flag itself,
The flag is : nactf{un10ck_th3_s3cr3t5_w1th1n_cJfnX3Ly4DxoWd5g}
Task: General Skills (Survey)
Description:
Fill out this survey for a flag.
You can just fill out the survey and while submitting it reveals the flag.
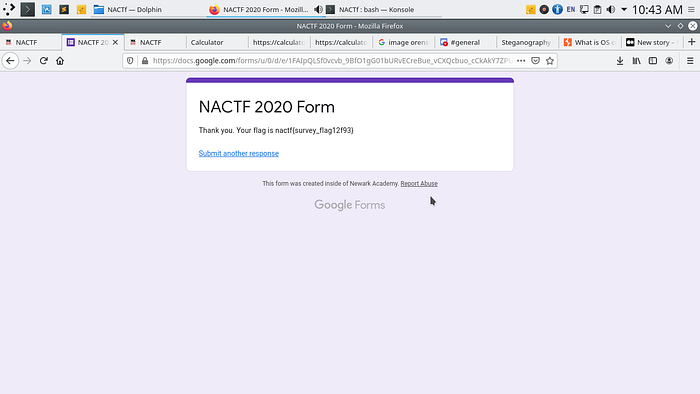
The flag is: nactf{survey_flag12f93}
Task: General Skills (Join the Discord)
Description:
Join the NACTF 2020 Discord and find the flag!
You can just join the NACTF’s discord and it will pop the flag when you finished joining the discord.
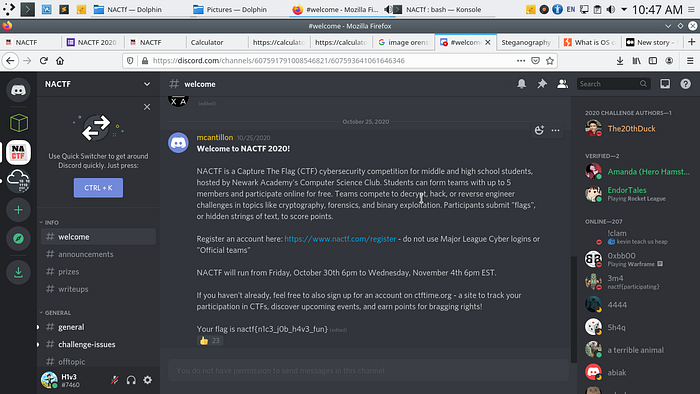
The flag is: nactf{n1c3_j0b_h4v3_fun}
Task: General Skills (Intro to Flags)
Description:
NACTF flags are case-sensitive and should be inputted with the format nactf{…}
Practice entering your flag here: nactf{fl4gz_4_d4yz}
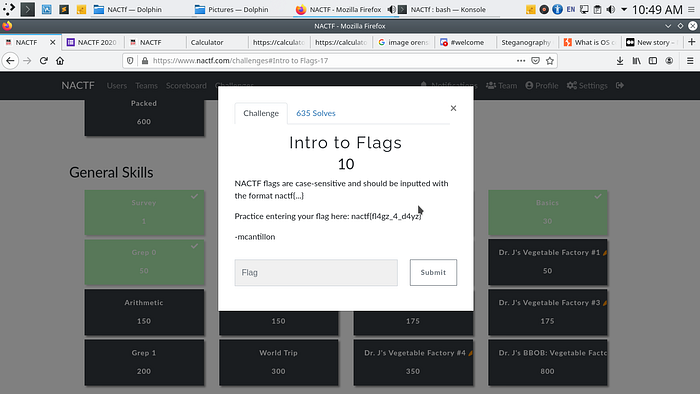
Just enter the given flag and you’re good to go.
The flag is : nactf{fl4gz_4_d4yz}
Task: General Skills (Basics)
Description:
Tiffany no longer communicates in normal text. Weird, I know. She randomly sent me this message: bmFjdGZ7YmE1MzVfYXIzX3N3MzN0fQ==
Can you figure out what it means?
The task is to figure out the flag in the given message “bmFjdGZ7YmE1MzVfYXIzX3N3MzN0fQ==”, Seems like the given message is of Base64 and how did i find it?
Simple basically Base64 ends with “==”. So we just have decode base64 to readable format. You can use echo command with base64 — decode by piping it together.
The command is :
echo “bmFjdGZ7YmE1MzVfYXIzX3N3MzN0fQ==” | base64 — decode
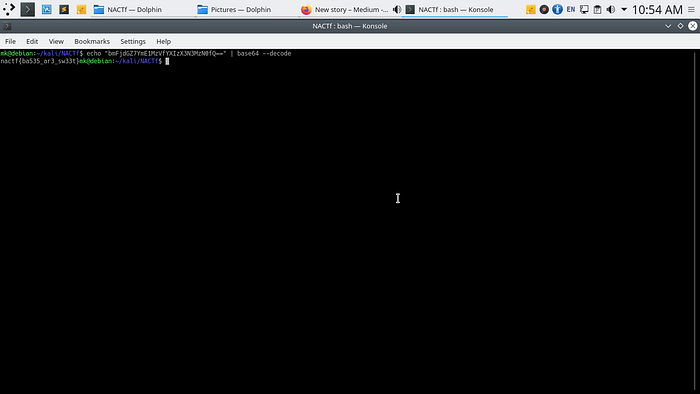
The flag is: nactf{ba535_ar3_sw33t}
Task: General Skills (Grep 0)
Description:
Sophia created this large, mysterious file. She might have said something about grap.. grapes? Find her flag!
link:
https://www.nactf.com/files/c5a4ac173dc86dfe519aefef502c388e/flag.zip
The given task is to find the flag in the given text file. Since the given file is so large and it is relatively impossible to find the flag if we have to read the whole text file line by line.
Instead you can just cat the whole file and pipe it to grep command to find the flag. The hint given is to find the line some what similar to “grap.. grapes”. so we just have to use the following command,
Command:
mk@debian:~/kali/NACTf/New Folder$ ls
flag.txt flag.zip
mk@debian:~/kali/NACTf/New Folder$ cat flag.txt | grep “gr”
nactf{gr3p_1s_r3ally_c00l_54a65e7}
mk@debian:~/kali/NACTf/New Folder$
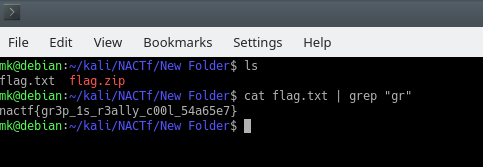
The flag is: nactf{gr3p_1s_r3ally_c00l_54a65e7}
Task: General Skills (Hashbrowns)
Description:
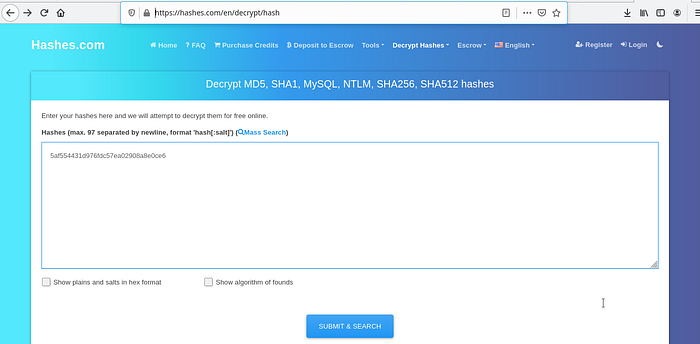
MD made 5 hashbrowns this morning and forgot to add salt and pepper. He took a bite out of one of them and found a piece of paper with this written on it: 5af554431d976fdc57ea02908a8e0ce6.
From the description we know that the given hash is “MD5 Hash”. So you just have to decode the given hash to readable Format.
You can use HashCat or any Online Decryption tool to decrypt the given hash. For time-saving purpose i used https://hashes.com/en/decrypt/hash to decrypt my hash.
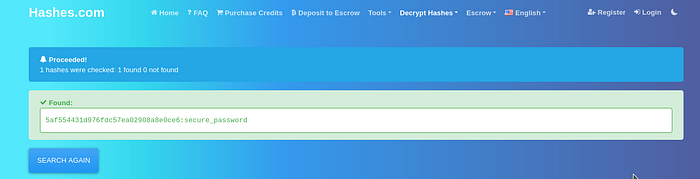
The flag is: nactf{secure_password}
Task: Cryptography (Caesar’s Challenge)
Descryption:
Zabelo wrote this message on a note he passed to me. anpgs{q3p1cu3e1at_e0px5!} He also told me his favorite number was 13. What could this mean?
The challenge is to decrypt the flag given in Caesar Crypt format Caesar’s Challenge is a historical cryptography challenge which uses rotational encryption. By the given hint it uses rot13 format, so we just have to rotate the given crypt 13 time all over one by one. So we just can automate this stuff in our Linux terminal by combining echo and tr command,
Command:
echo ‘anpgs{q3p1cu3e1at_e0px5!}’ | tr ‘A-Za-z’ ‘N-ZA-Mn-za-m’
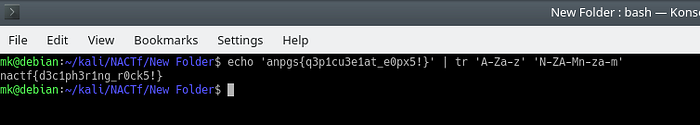
The flag is: nactf{d3c1ph3r1ng_r0ck5!}
Task: Cryptography (YAMS)
Description:
Instead of turnips, Yavan loves YAMS. Day and night, he sings about YAMS, dreams about YAMS and runs to the store to catch the newest released batch of YAMS. Hes cryptic too. I wonder what this could mean.
Uexummq lm Vuycnqjc. Hqjc ie qmud xjas: fycfx{waY5_sp3_Y0yEw_w9vU91}
Hint: I can’t believe he also eats them with vinaigrette!
If you have ever wondered what YAMS is it is a Sweet Potato. By the given hint Yavan loves YAMS which means he likes Sweet Potato and then they say that he’s cryptic. So we just have to assume that he used some cryptographic technique to hide the message. By viewing the second hint it says, “I can’t believe he also eats them with vinaigrette!”. Vinaigrette is a well known cryptographic technique among cryptographer’s which is commonly called as “Vigenere Cipher”.
So for this task we can use an online tool to de-cipher it, use the link below,
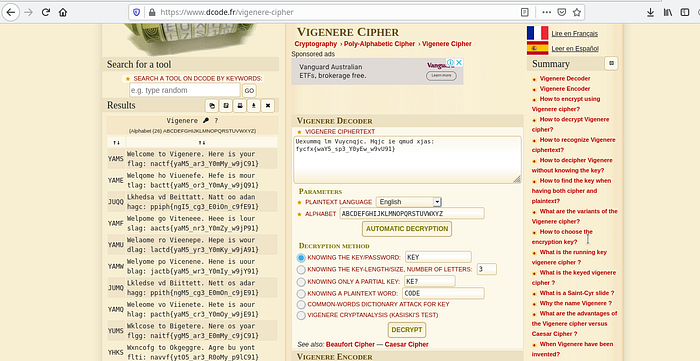
This site automatically de-cipher’s the code to all possible forms and the first result is our flag.
Result:
Welcome to Vigenere. Here is your flag: nactf{yaM5_ar3_Y0mMy_w9jC91}
The flag is: nactf{yaM5_ar3_Y0mMy_w9jC91}
Task: Forensics (Gummies)
Description:
Kylie is obsessed with gummies. With her collection of miscellaneous gummy bears, she took this incredible picture which is now her phone’s wallpaper. Can you find her flag?
First thing to do with image in forensics is to analyze the image and try basic stenographic analysis.
For this task we would be using the tool called steg-solve. I’d be using online version of steg-solve using the link below,
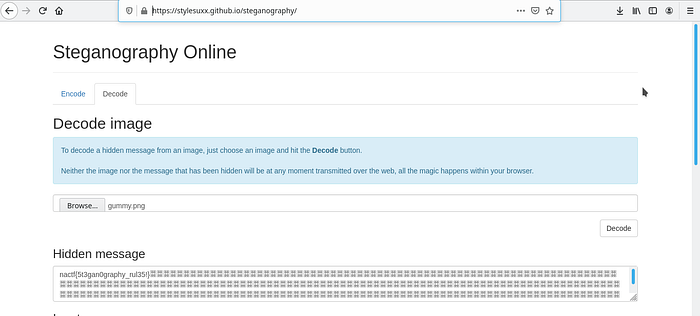
The flag is: nactf{5t3gan0graphy_rul35!}
Task: Forensics (Meta-morphosis)
Description:
Mikey really likes Metamorphosis by Franz Kafka, so much so that he sent this meme to the class.
link:
https://www.nactf.com/files/6d05823012a6a8f126ea68950e894e5e/meme-3.jpg
From the description we know that the flag is hidden inside the image’s metadata. So we just have to view the meta-data of the image.
For this task we can use online Image — Forensics tools like,
I’m going to use FotoForensics tool for my task,
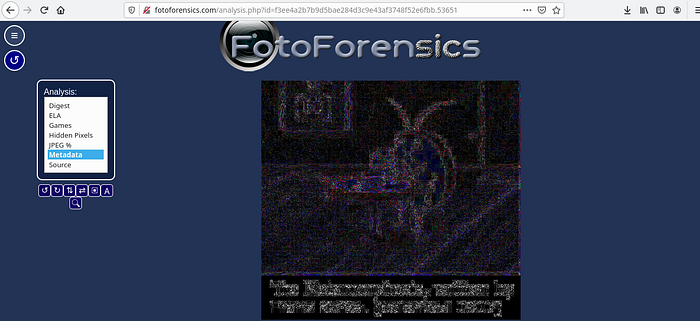
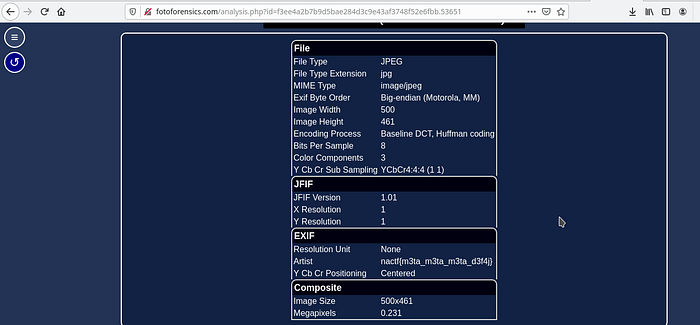
The flag is: nactf{m3ta_m3ta_m3ta_d3f4j}
Task: Forensics (Turnips)
Description:
Dr. J loves his ch0nky turnips, can you find his ch0nky flag?
link:
https://www.nactf.com/files/b1a2f3283feb2e533bff9395aa387bcf/turnip-for-what.jpg
From the description I tried using steg-solve and foto-forensics. But it didn’t drop anything useful for me. So I’m going to use 29a.ch tool to extract the strings in it,
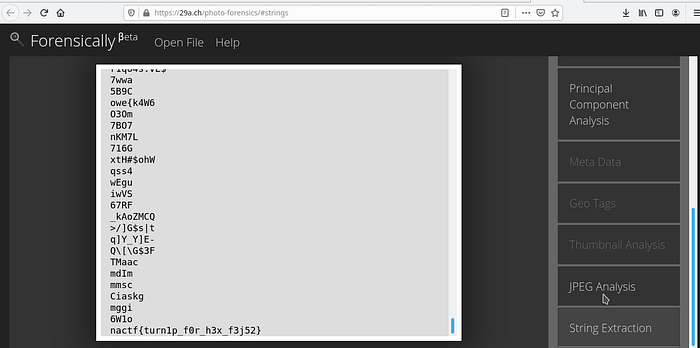
The flag is: nactf{turn1p_f0r_h3x_f3j52}
Task: Forensics (Secret Message)
Description:
Monica loves inventing secret languages. So much so that she claims to be the only one to know the message in this recording. What does it say?
link:
https://www.nactf.com/files/24bd186de748332b30614a353cb64ab1/flag.mp3
For this task i was literally wondering how could i do Forensics on a mp3 file. So i just played the audio file and listened to it. While i was analyzing the sounds in the audio file resembled Morse-Code. So i just have to find the test equivalent to the Morse-Code in it. To make my task easier i used an online tool to decrypt the message. The link for the tool is provide in the link below,
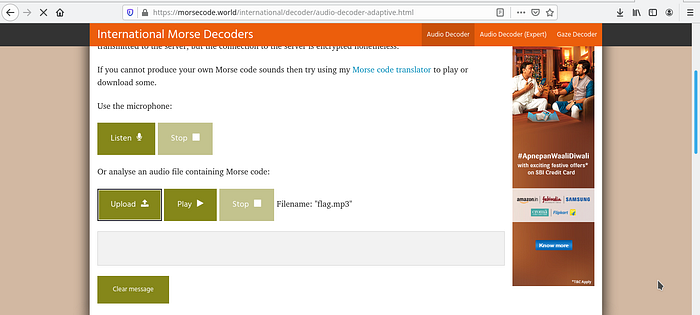
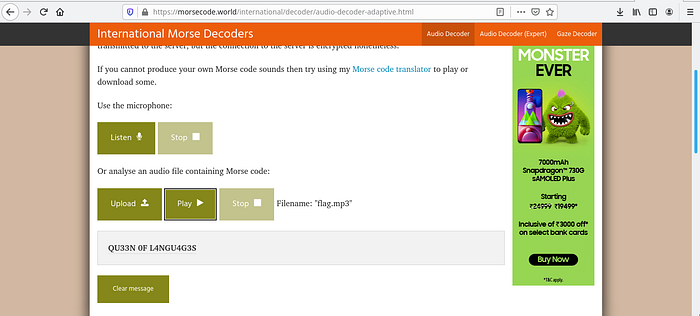
The flag is: nactf{QU33N 0F L4NGU4G3S}
Task: Forensics (Turnips 2)
Description:
Uh oh.. Parth’s file seems to have been corrupted. Can you figure out how to find his flag?
Hint: File headers are important, aren’t they?
By the given hint we get to know that the file is corrupted due to header change. So all we have to do is to change the header of the file to view the flag. Use Hex Editor to change the Header of the file to PNG header to make it reveal the flag.
The flag is: nactf{th3_turn1p5_ar3_tak17g_0v35_skf9}
Task: WEB (Inspect)
Description:
Lola’s new to website-building. Having just learned HTML and CSS, she built this site and embedded some dark secrets. I wonder where I could find them.
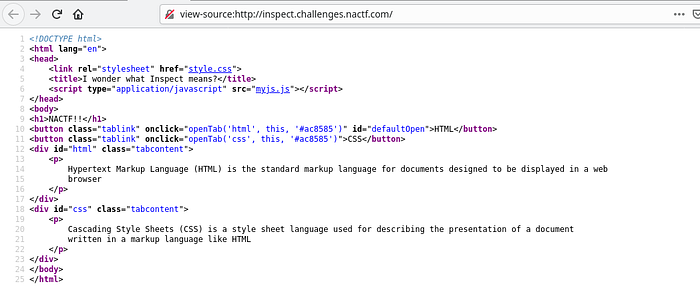
By analyzing the source code we couldn’t find the flag in it. But there are back links to CSS an JS file in the source code. Lets analyze the STYLE.CSS file first.
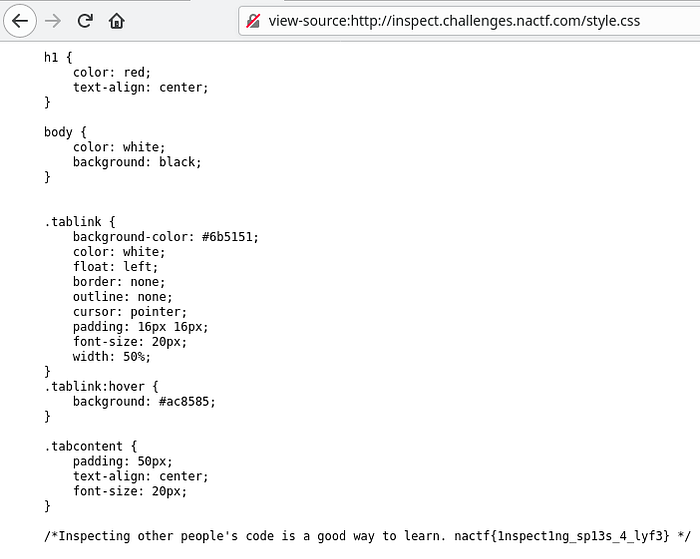
We just found the flag in the style.css file.
The flag is: nactf{1nspect1ng_sp13s_4_lyf3}
Task: WEB (Missing Image)
Description:
Max has been trying to add a picture to his first website. He uploaded the image to the server, but unfortunately, the image doesn’t seem to be loading. I think he might be looking in the wrong subdomain…
From the above description we know that file is in the website but it is pointing to wrong subdomain. By viewing its source we get,
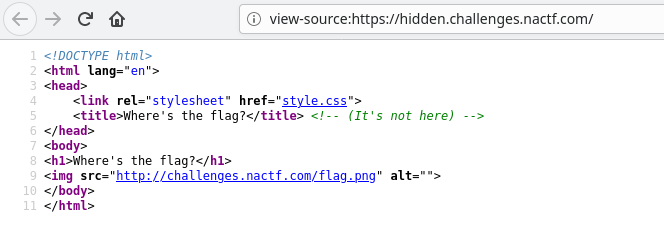
The image source links to http://challenges.nactf.com/flag.png which is the wrong subdomain. The correct subdomain is, http://hidden.challenges.nactf.com/flag.png
So we just have to browse to http://hidden.challenges.nactf.com/flag.png which results in,
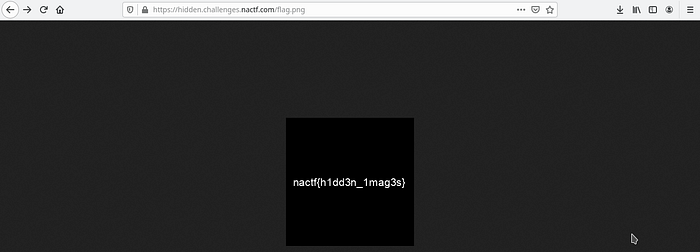
The flag is: nactf{h1dd3n_1mag3s}
Task: WEB (Forms)
Description:
Skywalker has created 1000 login forms and only managed to make one of them work. Find the right one and login! He also went a bit crazy with the colors for some reason.
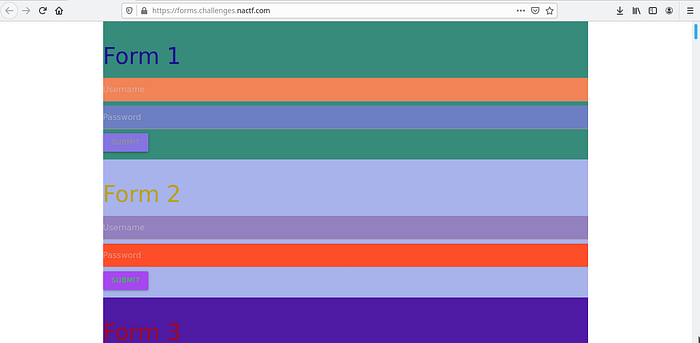
Since there are over thousand forms in this page, it’s nearly impossible to find the working one. From the hint we know that there is only one working form so we can assume that the working form will be the only one properly utilizing the backend Javascript code. We have to find the Javascript and analyze what function it uses,
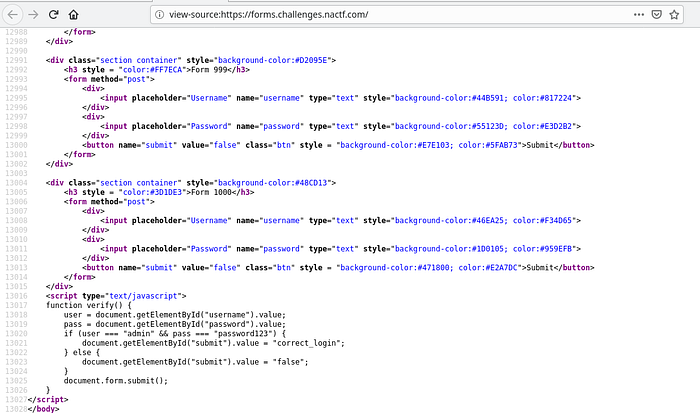
<script type="text/javascript">
function verify() {
user = document.getElementById("username").value;
pass = document.getElementById("password").value;
if (user === "admin" && pass === "password123") {
document.getElementById("submit").value = "correct_login";
} else {
document.getElementById("submit").value = "false";
}
document.form.submit();
}
</script>From the above JS we know that it uses function called verify(), we have to find the form that uses verify() function.
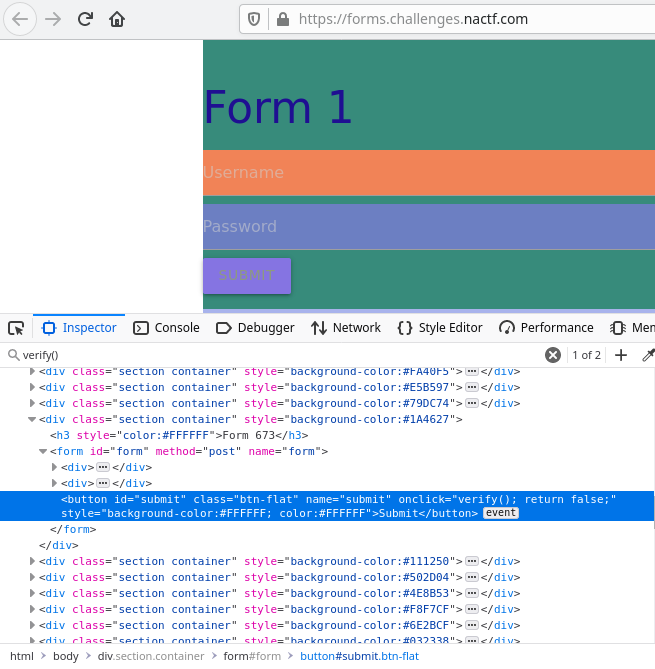
Since the form 673 is the one that uses verify() function, it is the only one that’s working.
From the JS we previously analyzed we know the login password,
if (user === "admin" && pass === "password123")we use this above information to login,
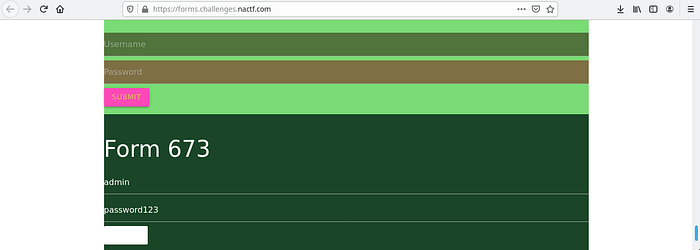
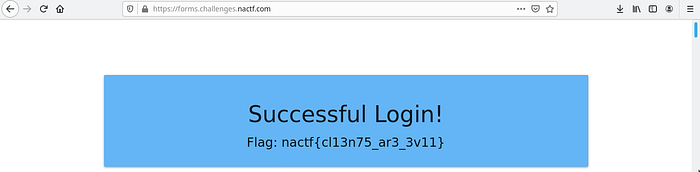
The flag is: nactf{cl13n75_ar3_3v11}
Task: WEB (Calculator)
Description:
Kevin has created a cool calculator that can perform almost any mathematical operation! It seems that he might have done this the lazy way though… He’s also hidden a flag variable somewhere in the code.
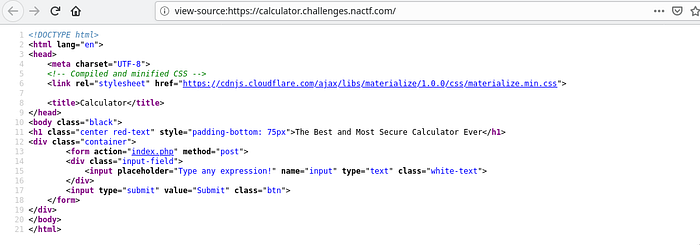
Lets view the source code of the website first before we take any actions,
By analyzing the calculator website we found that it is vulnerable to command injection. So let’s implement few OWASP codes to check it out.
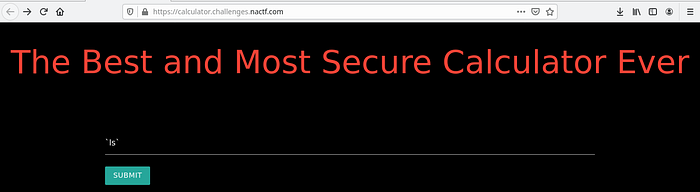
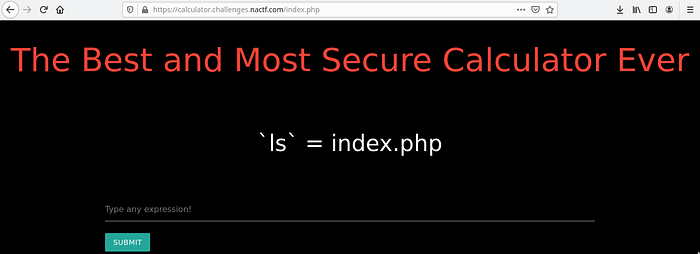
We found that it implemented the input as a bash command. So let’s try to execute OWASP Command Injection Script to trigger input field.
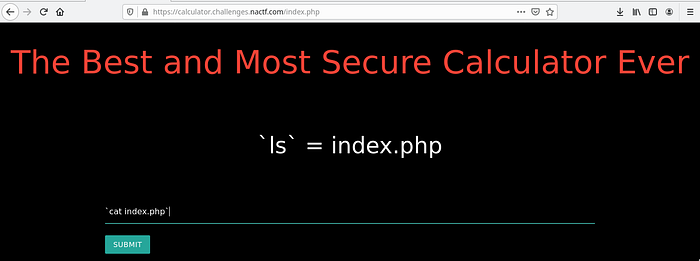
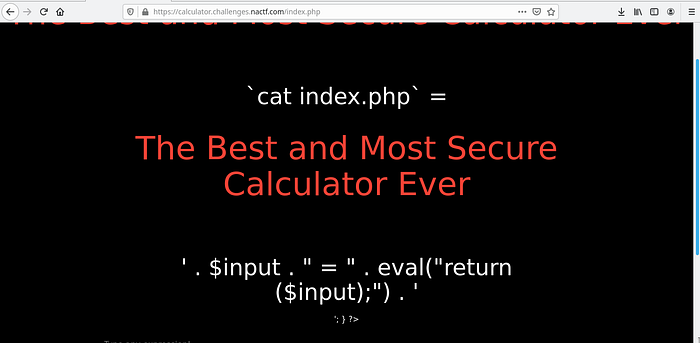
Okie now it executed our command now let’s take a look at the source code,
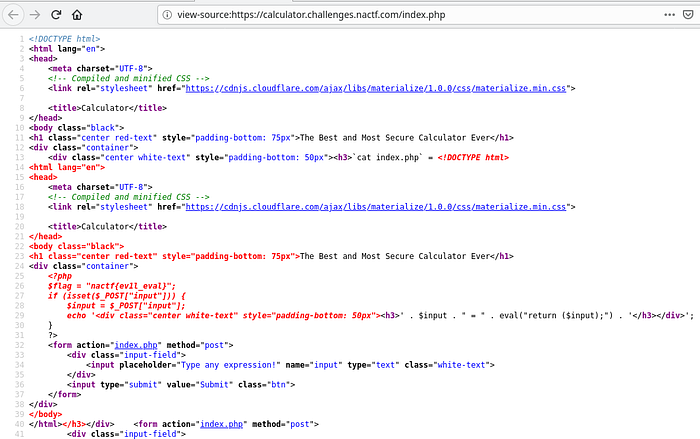
<div class="container">
<?php
$flag = "nactf{ev1l_eval}";
if (isset($_POST["input"])) {
$input = $_POST["input"];
echo '<div class="center white-text" style="padding-bottom: 50px"><h3>' . $input . " = " . eval("return ($input);") . '</h3></div>';
}
?>
<form action="index.php" method="post">
<div class="input-field">
<input placeholder="Type any expression!" name="input" type="text" class="white-text">
</div>
<input type="submit" value="Submit" class="btn">
</form>
</div>Now we just found the hidden flag in the source code.
The flag is: nactf{ev1l_eval}
Task: WEB (Cookie Recipe)
Description:
Arjun owns a cookie shop serving warm, delicious, oven-baked cookies. He sent me his ages-old family recipe dating back four generations through this link, but, for some reason, I can’t get the recipe. Only cookie lovers are allowed!
A common cookie configuration many sites use is setting the cookie to the root of the site with the Secure tag enabled, SameSite set to “None” or blank, and the word “Session” as the expiration age. When set like this, the cookie applies to anywhere on the site without expiration (until we close the browser or something). Let’s configure this and login.If done correctly, the flag should appear. $nbsp;
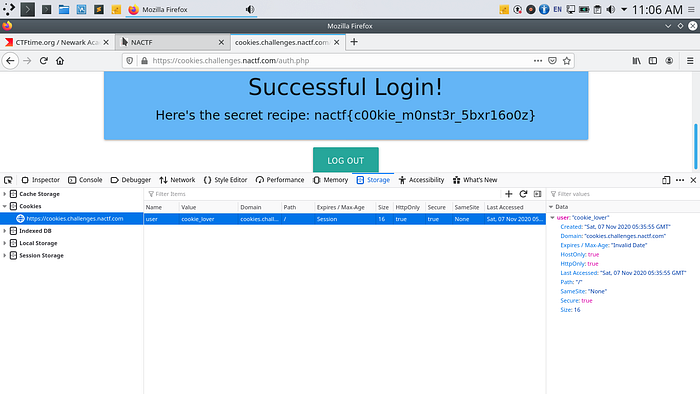
The flag is: nactf{c00kie_m0nst3r_5bxr16o0z}
Task: WEB (Login)
Description:
Vyom has learned his lesson about client side authentication and his soggy croutons will now be protected. There’s no way you can log in to this secure portal!
link: https://login.challenges.nactf.com/
Hint: https://xkcd.com/327/
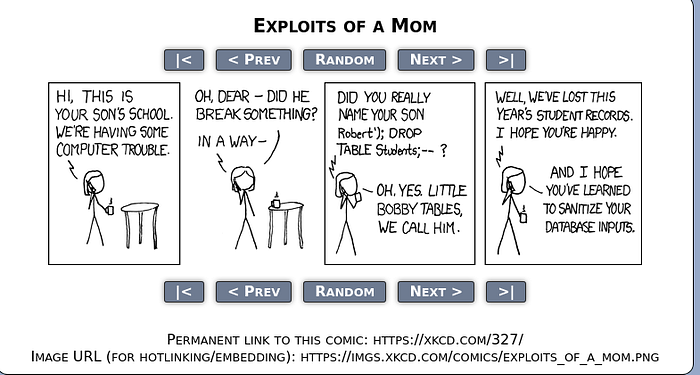
If we click the hint link, it takes us to a comic about a mom getting a call from her son’s school about the school records being deleted because of her son. The detail that stands out is the boy’s name.
Robert'); DROP TABLE students;--
By analyzing the given hint we can assume that its a typical “SQL Injection Vulnerability”.
You can use a common SQL Injection like,
Username: ' OR ''='
Pass: ' OR ''='
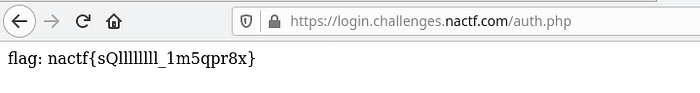
The flag is: nactf{sQllllllll_1m5qpr8x}
Scoreboard:
Category Breakdown:
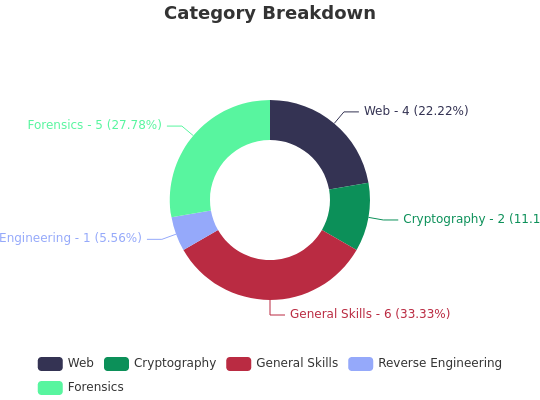
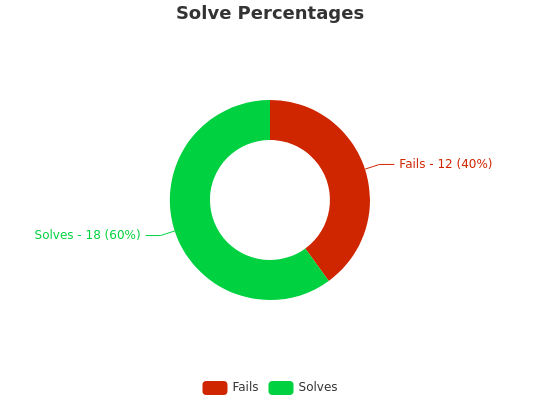
Solve Percentage:
Thanks for reading my walk-through solution’s on NACTF Challenge. See you again later on another exciting write-up, Bye.